Anthony M. McCartney
College of Science and Technology, Bellevue University
January 21, 2024
The McCumber Cube Model
The McCumber Cube, named after its creator, John McCumber, was created to manage network, domain, and internet protection as an expansion of the CIA Triad (Chappel, 2021). Its purpose was to give an organization a better view of its information assurance position.
Having three dimensions, it offers a holistic view of security, addressing the complexities of safeguarding information. These three sides represent goals, information states, and safeguards. Using the cube to look at risk from different angles provides the capability to see each identified risk from a different perspective (Price, 2008), thus allowing for a more complete solution at addressing that risk and validating the controls.
It is typically represented by a three-dimensional cube showing three sides that represent each of the primary focus groups, with each side having three sections which then represent each of the elements associated with the corresponding aspect (see Figure 1).
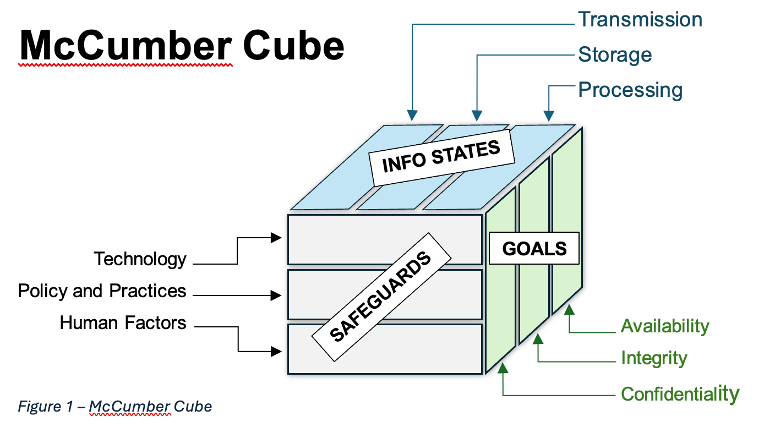
Goals
The first dimension of the cube is goals, which contains the original CIA Triad model. The elements of the triad are Confidentiality, Integrity, and Availability, which are defined by the Committee on National Security Systems Instruction Number 4009 (CNSSI-4009) are defined as follows (CNSS, 2022):
Confidentiality – The property that information is not disclosed to system entities (users, processes, devices) unless they have been authorized to access the information.
Integrity – The property whereby an entity has not been modified in an unauthorized manner.
Availability – The property of being accessible and useable upon demand by an authorized entity.
Information States
The second dimension of the cube focuses on information states, or where the data is located. The elements of this dimension are transmission, storage and processing. Knowing where the data is at any given time helps to know what risks and threats are associated with that location or locations.
Processing – Data is being created and updated.
Storage – Data is written. The information is now stored on a hard drive, in the cloud, on a USB or other physical media.
Transmission – Data is retrieved. The data is being moved from one location to another in the network and across systems for access.
Safeguards
The third and final dimension of the model is safeguards. This is the human aspect of the model, including policies and procedures, technology used, and training. The human aspect is most likely going to be the largest source of risk involved, so having the right education, policies, and software in place to mitigate that risk is essential.
Policies and Practices – Having C-Suite approved and enforced polices are key to make sure that addressed risks are limited or eliminated. Along with those polices should be outlined procedures or practices on how to fulfil the policy to ensure that the data is safe.
Technology – Using software or tools that have been evaluated and trusted to provide access to the data should be a priority. This could include network monitors or AV installed on workstations, or even a VPN to restrict access to secure networks or remote workers.
Human Factors – Education and awareness training should cover topics like common risks, legal compliance requirements, and corporate policies.
Practical Example
For law enforcement officers, having access to extremely sensitive information in their cruisers requires having a computer – or Mobile Data Terminal (MDT) – connected back to a server that can access the FBI CJIS system. While there are multiple security controls in place due to legal requirements and county policies, one piece of technology is paramount to the success of accessing the data, the VPN.
A VPN is required to ensure that the data in transmission is encrypted and secure as the MDT are connected to the main hub via cell service with air cards. While these air cards are placed on a public safety plan and system, there is still the possibility of snooping if someone managed to gain access to another card in the same network, got into the network via the provider, or any other number of sniffing and snooping methods. Having that VPN connection established moves the risk down to the client and server for mitigation as the traffic cannot be deciphered without the appropriate keys and certificates.
Conclusion
In conclusion, the McCumber Cube Model offers a comprehensive framework for understanding and managing information security within an organization. By encompassing the three critical dimensions of goals, information states, and safeguards, it builds upon the foundational principles of the CIA Triad, enhancing an organization’s ability to identify and address various risks associated with information security.
As cyber threats continue to evolve in complexity and sophistication, models like the McCumber Cube remain vital tools for organizations seeking to navigate the ever-changing landscape of information security. With its holistic approach, the McCumber Cube enables a thorough examination of potential vulnerabilities, fostering a security-conscious culture and guiding the implementation of effective, resilient security controls.
Sources
Chappel, M. (2021). Access Control and Identity Management, Third Edition. Jones and Bartlett Learning.
CNSS. (2022, March 2). Committee on National Security Systems (CNSS) Glossary. Retrieved from https://www.niap-ccevs.org/Ref/CNSSI_4009.pdf
Price, S. M. (2008). Extending the McCumber Cube to Model Network Defense. ISSA Journal, 14 – 17.


